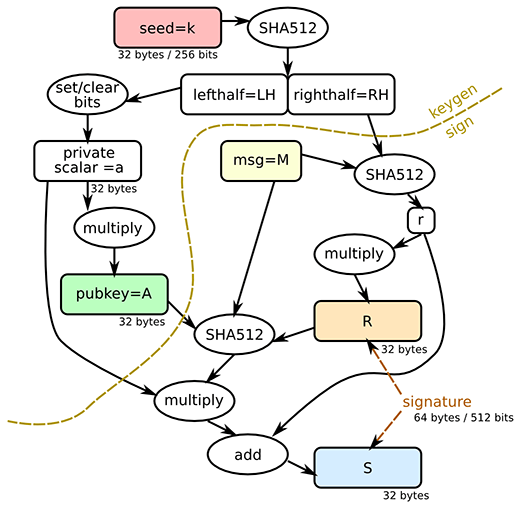
A Ruby binding to the Ed25519 elliptic curve public-key signature system described in RFC 8032.
Two implementations are provided: a MRI C extension which uses the "ref10" implementation from the SUPERCOP benchmark suite, and a pure Java version based on str4d/ed25519-java.
Ed25519 is one of two notable algorithms implemented atop the Curve25519 elliptic curve. The x25519 gem is a related project of this one, and implements the X25519 Diffie-Hellman key exchange algorithm on the Montgomery form of Curve25519.
What is Ed25519?
Ed25519 is a modern implementation of a Schnorr signature system using elliptic curve groups.
Ed25519 provides a 128-bit security level, that is to say, all known attacks take at least 2^128 operations, providing the same security level as AES-128, NIST P-256, and RSA-3072.
Ed25519 has a number of unique properties that make it one of the best-in-class digital signature algorithms:
- Small keys: Ed25519 keys are only 256-bits (32 bytes), making them small enough to easily copy around. Ed25519 also allows the public key to be derived from the private key, meaning that it doesn't need to be included in a serialized private key in cases you want both.
- Small signatures: Ed25519 signatures are only 512-bits (64 bytes), one of the smallest signature sizes available.
- Deterministic: Unlike (EC)DSA, Ed25519 does not rely on an entropy source when signing messages. This can be a potential attack vector if the entropy source is not generating good random numbers. Ed25519 avoids this problem entirely and will always generate the same signature for the same data.
- Collision Resistant: Hash-function collisions do not break this system. This adds a layer of defense against the possibility of weakness in the selected hash function.
You can read more on Dan Bernstein's Ed25519 site.
Is it any good?
Help and Discussion
Have questions? Want to suggest a feature or change? Join a discussion group:
- Crypto.rb Gitter: web-based chat about Ruby crypto projects including ed25519.
- Crypto.rb Google Group: join via web or email (crypto-rb+subscribe@googlegroups.com)
Requirements
ed25519.rb is supported on and tested against the following platforms:
- MRI 3.0, 3.1, 3.2, 3.3, 3.4
- JRuby 9.4.12, 10.0.0
Installation
Add this line to your application's Gemfile:
gem 'ed25519'
And then execute:
$ bundle
Or install it yourself as:
$ gem install ed25519
Usage
Require ed25519.rb in your Ruby program:
require "ed25519"Generate a new random signing key:
signing_key = Ed25519::SigningKey.generateSign a message with the signing key:
signature = signing_key.sign(message)Obtain the verify key for a given signing key:
verify_key = signing_key.verify_keyCheck the validity of a signature:
verify_key.verify(signature, message)The verify method will return true if the signature verifies, or raise
Ed25519::VerifyError if verification fails.
Serializing Keys
Keys can be serialized as 32-byte binary strings as follows:
signature_key_bytes = signing_key.to_bytes
verify_key_bytes = verify_key.to_bytesThe binary serialization can be passed directly into the constructor for a given key type:
signing_key = Ed25519::SigningKey.new(signature_key_bytes)
verify_key = Ed25519::VerifyKey.new(verify_key_bytes)Security Notes
The Ed25519 "ref10" implementation from SUPERCOP was lovingly crafted by expert security boffins with great care taken to prevent timing attacks. The same cannot be said for the C code used in the ed25519.rb C extension or in the entirety of the provided Java implementation.
Care should be taken to avoid leaking to the attacker how long it takes to generate keys or sign messages (at least until ed25519.rb itself can be audited by experts who can fix any potential timing vulnerabilities)
ed25519.rb relies on a strong SecureRandom for key generation.
Weaknesses in the random number source can potentially result in insecure keys.
Contributing
Bug reports and pull requests are welcome on GitHub at https://github.com/RubyCrypto/ed25519. This project is intended to be a safe, welcoming space for collaboration, and contributors areexpected to adhere to the Contributor Covenant code of conduct.
License
Copyright (c) 2012-2025 Tony Arcieri. Distributed under the MIT License. See LICENSE for further details.
Code of Conduct
Everyone interacting in the ed25519.rb project’s codebases, issue trackers, chat rooms and mailing lists is expected to follow the code of conduct.